Funny Memes or Phishing, Identity Theft and Exploitation?
By Olga Detrixhe, Nex-Tech
We have all noticed a surge in funny Facebook memes and games while sheltering in place during the COVID-19 pandemic. They are so clever and ridiculously tempting to click-and-share or click-and-play along. But here is the rub. There is an increased likelihood that clicking, playing, and entering information really just opens the door wide open for cyber predators to get your information.
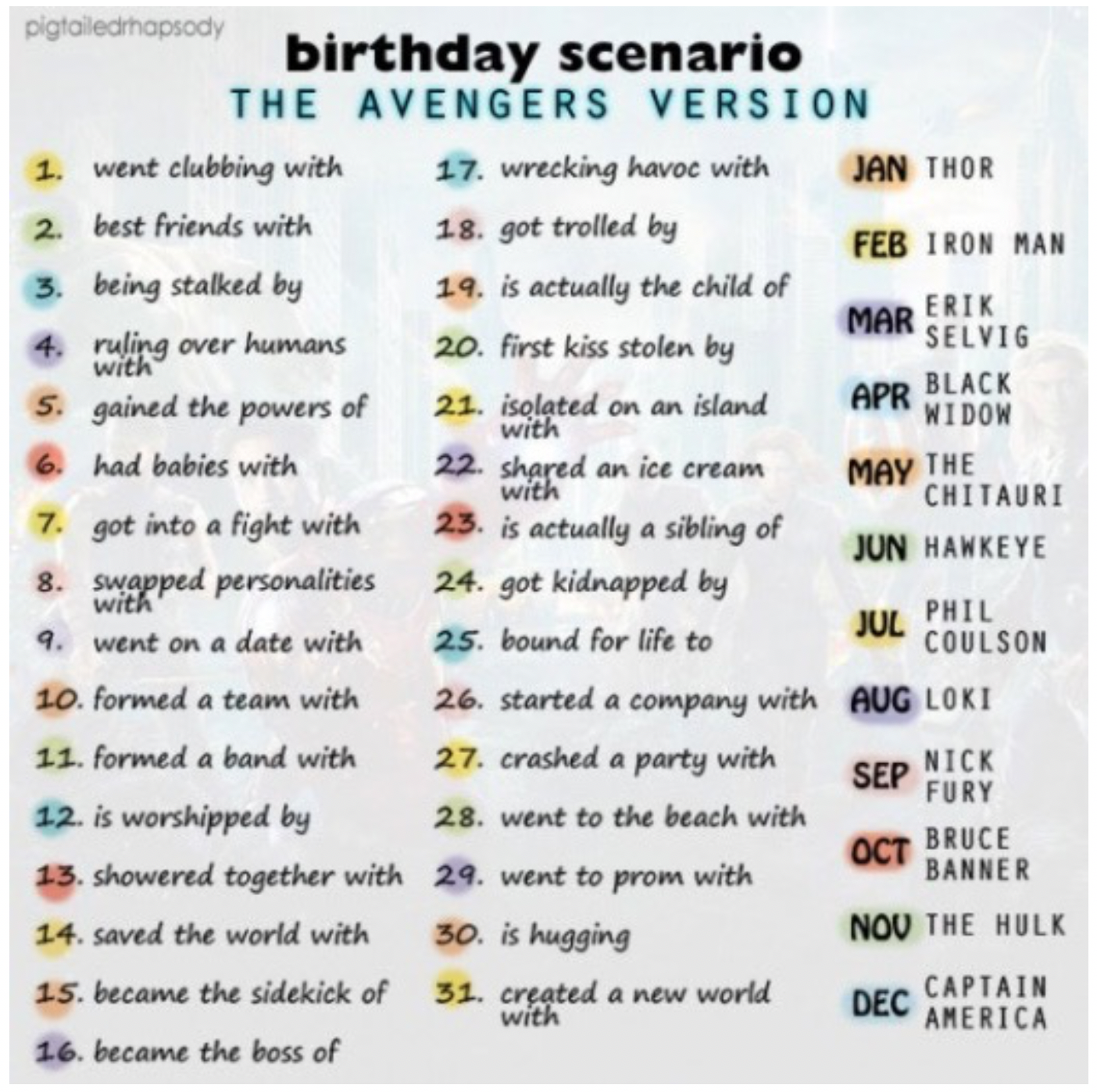
Play along for a moment. Have you ever posted your mother’s maiden name plus your favorite food item to see what your band name is? What about entering your birthday and month, to find out which Avenger superhero you are? Or was your submission a graduation year, high school and a picture to support the graduating class? Whatever seemingly harmless, silly or even inspirational game or meme, there is a good chance it is not. So why do tens of thousands of people play along? Why do they give away personal information then share it with friends? Likely because those bits and pieces seem meaningless.
But they are not. Those pieces create a much bigger data set. See, the bad guys are smart. They do not ask for personal information outright. No. Instead they merge innocuous info with the good stuff until that data can be mined. Then pertinent bits and pieces get extracted and used to penetrate security or verification questions to online accounts.
It is not news that criminals exploit vulnerabilities, but it has become so familiar to give away data as part of our digital footprint that we sometimes forget we could actually be inviting criminals right into our private lives. In fact, according to an article posted on thehill.com, the FBI reports an increase in daily cybersecurity complaints, up from around 1,000 before coronavirus to upwards of “…between 3,000 and 4,000.” So now more than ever, is not the time to compromise convenience for security.
Now take that a step further to the virtual world of work and school.
Ever wonder what might cause the perfect cyber storm? Well, it is the onset of COVID-19, followed by sheltering in place and a rapid increase in use of technology outside of an IT-reinforced environment. It is stress and dealing with massive change. It is trying to get logged into that video call while getting kids set up for school. It is taking advantage of cloud apps from a virtual environment without a second thought. It is not ensuring the usual firewalls and protections are in place at home as we access the cloud apps that have given us the freedom and flexibility during COVID-19.
And cyber criminals get better every day. Take email for example.
See, phishing emails are no longer full of grammatical errors. Nobody is claiming to be a long lost relative or the Prince of Zamunda who wants to give you money but needs your banking information to do it. Today’s phishing attacks are highly sophisticated and often look real—even to the trained eye.
Here is how it can happen. Microsoft, the name on products many of us use every day, always ranks among top impersonated brands. Phishing emails claiming to come from Microsoft look real and contain believable calls to action like “click here to avoid deactivation.” It seems real and deactivation is scary, so you are tempted to click. You are used to solving problems online. But, this time, clicking that link shoots you to a fake login page and voila, they have your credentials. Now, they have access to your email and all kinds of information like who you bank with, or the 401k paperwork you sent to HR, or previous posts or logins to Facebook, or potential answers to security questions. And you did not realize it, but you just voluntarily provided all the information needed to steal your identity, money, and business. Pretty creepy, huh? And the only clue that it was phishing and not Microsoft were slightly ‘off’ colors and some altered language.
So, what is the answer?
First, and always, be suspicious and vigilant ANY time you are online. That means Facebook, Instagram, email, that dating site, everywhere.
Then, if it happens to you, if your information is compromised or shows up on the dark web, start fighting back and protecting your stuff. Here is how.
Use password managers to help cut down on re-using passwords and prompt you to change them regularly. Although they have flaws (like the fact that they’re still using a master password for protection), Kevin Mitnick would recommend them.
Check out the top 10 password apps for 2020: Consumer Advocate - Best Password Apps 2020.
Use Multifactor Authentication (MFA) whenever you can! Most mainstream cloud services already offer it, so check your account settings on EVERY important service you use and activate MFA. For your business, it’s worth investing into a paid MFA app, such as Duo, so you can protect key applications and manage users and access centrally.
Educate your staff. Humans are the single biggest security risk, so it is worth investing in making sure they know how to protect your business and not fall for phishing attacks. Talk to your IT provider for options.
Do not fall for ploys on social media. Security experts agree that a multitude of password clue pitfalls phishing for security questions can be found on social media. Check out the Identity Theft Resource Center for an overview on how not to overshare information just to find out your “dragon name”.
Always hover over email or web addresses to check the actual source. Do not fall for the phishing scams as outlined in the example above.